Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Would you like to insight in your inbox? Register for our weekly newsletters to only receive the company manager of Enterprise AI, data and security managers. Subscribe now
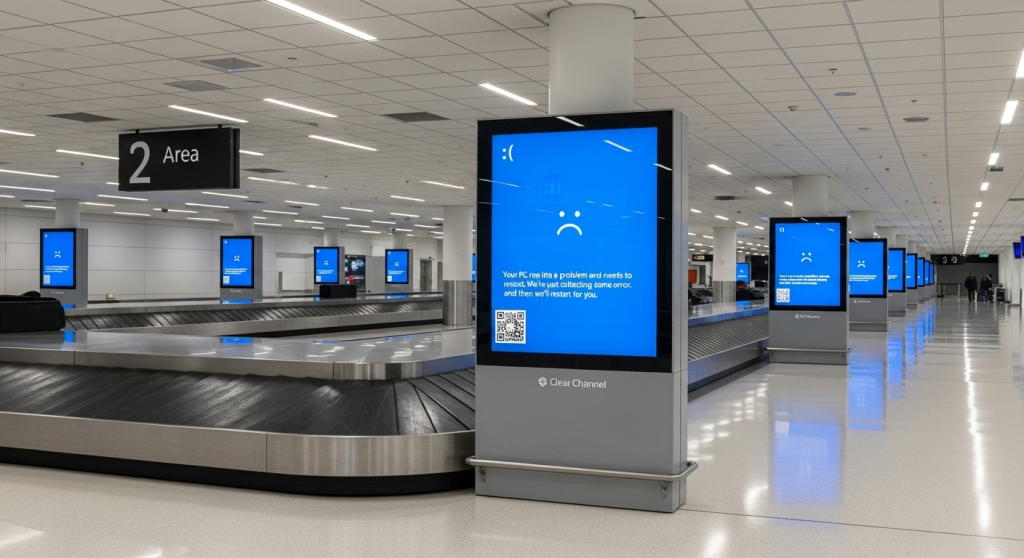
As we wrote in ours First analysis of the crowdstrike incidentThe failure on July 19, 2024 served as a strong memory of the importance of cyber resistance. Now, a year later, both Crowdstrike And the industry has experienced a significant transformation, with the catalyst of 78 minutes being powered that changed everything.
“The first anniversary of July 19 marks a moment when we deeply influenced our customers and partners and one of the decisive chapters in the history of crowdstrike became” Blog Detailing the company’s one -year trip towards improved resilience.
The numbers remain sobering: a faulty channel file 291 -update, which was provided at 04:09 UTC and was only 88 minutes later, crashed 8.5 million Windows systems worldwide. The insurance estimates made losses to 5.4 billion US dollars for the top 500 US companies alone, whereby the aviation with 5,078 flights worldwide was particularly strong.
Team cry, Senior Vice President for product and portfolio at TelesignA proximus global company interferes why this incident resonates a year later: “A year later, the crowdstrike incident will not only be remembered, it is impossible to forget. A routine software -update that is used without malicious intent and is rolled back in just 78 minutes, it was still possible to dismantle critical infrastructure worldwide.
The AI Impact series returns to San Francisco – August 5th
The next phase of the AI is here – are you ready? Join the managers of Block, GSK and SAP to get an exclusive look at how autonomous agents redesign of decision-making from real time up to end-to-end automation.
Secure your place now – space is limited: https://bit.ly/3guuplf
Its technical analysis shows unpleasant truths about the modern infrastructure: “This is the real wake -up call: Even companies with strong practices, a staged rollout, fast rollback, can enable the risks that are introduced by the infrastructure, which enable, quickly, cloud native, the same speed.
The cause of crowdstrike resulted in a cascade of technical failures: a false adjustment between input fields in your IPC type, lack of time -array -array limits and a logic error in your content validator. These were not marginal cases, but fundamental quality control gaps.
Merritt Baer, in -depth Chief Security Officer at Encrypt Ai And consultants from companies, including Andesit, provides a decisive context: “Crowdstrikes failure was humble. It reminded us that even really large, ripe shops are sometimes wrong. This special result was a chance on a certain level, but it should never have been possible.
Your assessment is direct, but fair: “Had crowdstrike introduced the update in sand boxes and only sent it in steps in steps, as it was in front of Best Practice, it would have been less catastrophic, if at all.”
However, Baer also recognizes the answer from Crowdstrike: “The Comms strategy of Crowdstrike has shown good property of managers. The managers should always take over owners -it is not the fault of the intern. If their junior operator can understand it, it is my fault. It is our fault as a company.”
George Kurtz, founder and CEO of Crowdstrike, illustrates this owner principle. In A LinkedIn Post Kurtz wrote about the anniversary and wrote: “A year ago we confronted a moment when everything was tested: our technology, our operations and the trust that others have recorded in us. As a founder and CEO, I have taken this responsibility personally. I have and will always do it.”
His perspective shows how the company channeled the crisis in transformation: “What defined us was not this moment; it was all that came next. From the beginning, our focus was clear: Build an even stronger crowdstrike that was based on resistance, transparency and tireless execution. Our Nordstern was always our customers.”
The reaction of crowdstrike focused on her resilient after design framework, which Sentonas go beyond “quick corrections or improvements at the surface level”. The three pillars of the frame, including fundamental, adaptive and continuous components, represent a comprehensive rethinking of the functioning of the safety platforms.
The most important implementations include:
“We not only added some content configuration options,” emphasized Sentonas in his blog. “We basically considered how customers interact with the security platforms for companies and they could control them.”
The incident forced a broader settlement on provider dependencies. Baer strongly frames the lesson: “A huge practical lesson was that your provider is part of your supply chain. As CISO, you should test the risk of aware of it.
The failure of crowdstrike has changed the evaluation of the providers permanently: “I see that effective CISOS and CSOs that use these lessons to use the companies they want to work with and the security they receive as a product of the common business.
Sam Curry, Ciso at Zscaler, Added: “What happened to crowdstrike was unhappy, but it could have happened to many, so we may not have given them the blame with the advantage of afterwards. I will say that the world has used this to concentrate and attract more attention to the resistance, and this is a profit for everyone, since our collective goal is to make the Internet more secure and safer for the Internet.” For everything. “For everything.” For everything. “For everything.” For everything that is safe for everything. “
The analysis of Schreier extends beyond the basic security architecture: “The speed of scaling is associated with costs. Each routine update now has the weight of the potential systemic failure. This means more than testing. Telemetry may be precisely required. “
His most critical knowledge deals with a scenario that many had not considered: “And when the telemetry becomes dark, you need to need failed safe that assume that the visibility may disappear.”
This is a paradigm shift. How Schreier comes to the conclusion: “Because security is not just about keeping attackers away today, it is about being the only point of failure.”
Baer has already seen the next development: “Since Cloud, it has made it possible for us to use infrastructure as a code, in particular that AI enables us to make security differently, I look at how infrastructure decisions with autonomic and effective risks for process obligations, especially in the private risk situation, with autonomic danger processes, especially for the private.
The future -oriented initiatives of Crowdstrike include:
A year later, the transformation is obvious. Kurtz reflects: “We are a stronger company today than a year ago. The work continues. The mission remains. And we move forward: stronger, more intelligent and even more committed than ever.”
In his honor, Kurtz also recognizes those who stood by the company: “For every customer who stayed with us, even if it was difficult, thanks for their permanent trust. For our incredible partners who stood with us and raised our sleeves, thank you for being our extended family.”
The inheritance of the incident goes far beyond crowdstrike. Organizations are now implementing staged rollouts, maintaining manual overwriting functions and plan if security instruments may fail themselves. Supplier relationships are evaluated with new stricts and recognize that in our interconnected infrastructure, every component is of crucial importance.
As Sentonas recognizes: “This work is not yet finished and it will never be. Resilience is not a milestone; it is a discipline that requires continuous commitment and evolution.” The crowdstrike incident of July 19, 2024 is not only reminded because of the disorder that it caused, but also for the catalyted industry-wide evolution in the direction of true resistance.
Crowdstrike and the wider security ecosystem have emerged with a deeper understanding to ensure that the protectors themselves cannot harm themselves. This lesson, which was learned in 78 difficult minutes and a year of transformation, could prove to be the most valuable legacy of the incident.